We are pleased to announce the General Availability (GA) of Attack simulation training in Microsoft Defender for Office 365. Delivered in partnership with Terranova Security, Attack simulation training is an intelligent social engineering risk management tool that automates the creation and management of phishing simulations to help customers detect, prioritize and remediate phishing risks by using real phish and hyper-targeted training to change employee behaviors.
Emulate real threats with intelligent simulations
Intelligent simulations automate simulation and payload management, user targeting, schedule and cleanup. In the Microsoft 365 Security Center, administrators can launch a simulation and choose a technique commonly used by attackers and target users.
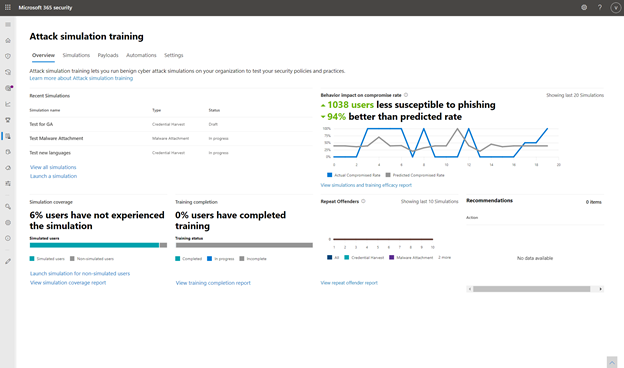
Attack simulation training dashboard
Wide variety of Phishing Techniques
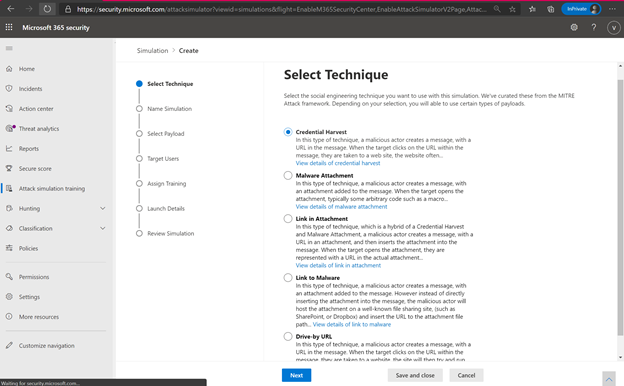
Following the simple steps outlined in the workflow, administrators can choose from the top five social engineering techniques and select the phish template from a list of real attacks seen in their tenant. Optionally customers can upload their own template and then select the users to whom the simulation will be sent.
Phishing Techniques available
Phish Template Library from Real Phish Emails
To maximize accuracy, Attack simulation training pulls its phishing templates from real world phish attackers seen in the customers environment. The security administrator can automate a “payload harvester” that collects and neutralizes phish emails received by the organization.
Payloads Available
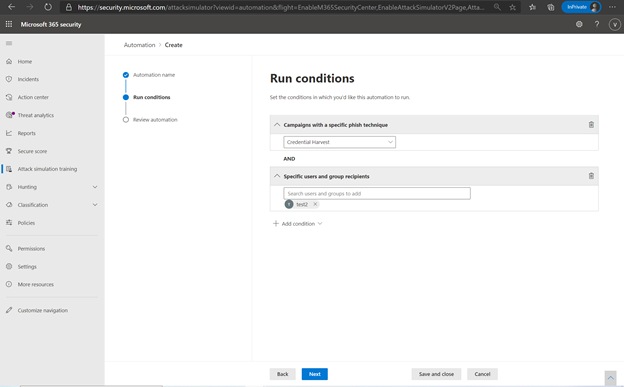
Through the real payload harvester, Attack simulation training trains employees to identify and report the kinds of emails real attackers will send them. The security administrator can set up targeted payload harvesting as well, using conditions like technique used, department targeted and frequency.
Payload Harvesting Conditions
Finally, security administrators can add ‘phishing indicators’ like an incorrect domain name, an urgency tip or a misspelled company name to train end users on commonly-seen phishing indicators.
Add indicators to phishing templates
User targeting and training assignment
User targeting is automated, and the administrator can use any address book properties to filter for a user list and target them. The administrator can also quickly import a list of “repeat offenders” or employees who have failed a simulation in the past and target the simulation to this group.
Target users based on address book filters
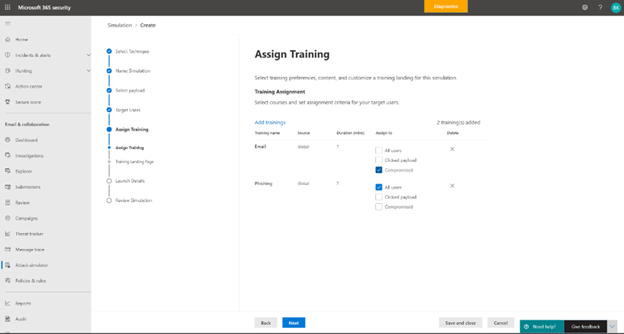
The administrator can then assign training tailored to a user’s behavior in the simulation. Microsoft recommends training to assign based on learning pathways and our intelligence into which training is effective for which kinds of behavior. The administrator can also choose to assign training themselves. For example, an administrator may choose to assign 3 trainings to users who were compromised in the simulation but only 2 to those who clicked and 1 to all users. The landing page on which the end user will land to access this training are wholly customizable for the look and voice of your brand. Finally, the administrator has the option to schedule the simulation to launch right away or at a later time, which can be customized by recipient time-zone.
Assign Training
Customized Role Based Access ensures that administrating the simulation and training is a secure and diversified workflow.
Quantify social engineering risk and prioritize remediation through training
The training effectiveness metric, which plots your organization’s actual compromise rate in a simulation against Microsoft’s predicted compromise rate, measures the effectiveness of the training program. Overlay the dates of training completion and simulations to correlate which trainings caused a drop in compromise rate and evaluate their effectiveness.
Training Effectiveness Report
Gain visibility over your organization’s training completion and simulation status through completeness and coverage metrics and track your organization’s progress against the baseline predicted compromise rate. Every reporting dashboard can be filtered in different ways and exported for reporting. Multiple reporting views allowing you to drill down on training efficacy, training completion, repeat offenders and coverage.
Reinforce the human firewall with industry-leading Security Awareness Training
Terranova Security’s huge library of phish training content enables personalized and highly specific training targeting based on the user’s behavior during a simulation.
Training Library
Nanolearnings, microlearnings, and interactivity
cater to diverse learning styles and reinforce awareness. Additionally, all trainings are available in 40+ languages and accessible to the highest standards to meet the needs of Microsoft’s global customers.
Attack simulation training enables organizations to improve their security posture by training their employees effectively and changing risky behavior. Organizations can choose from multiple training options to best fit their needs – using Microsoft’s recommended learning pathways, choosing to assign training manually, or choosing not to add training to a simulation.
E3 Trial
As Microsoft mentioned in their blog announcing the expansion of public preview to E3 license holders, we will continue to offer a subset of Attack simulation training capabilities to E3 customers as a trial. The trial offering contains the ability to use a Credential Harvest payload and the ability to select from 2 training experiences ISA Phishing and Mass Market Phishing. The trial offering will not include any other phishing techniques, automated simulation creation and management, conditional payload harvesting, and the complete catalog of Terranova Security trainings.
To get started today, go to Attack simulation training in your M365 Security and Compliance Center or use this link: aka.ms/AttackSim.